What is a Certificate of Destruction?
A Certificate of Destruction (CoD) is an audit document affirming that all confidential data stored on IT assets like hard drives, tapes, SSDs, PCs, laptops, Macs, Servers, or other storage media was successfully destroyed. It ensures that the organization or the service provider destroying data is following a reliable data destruction process in compliance with global data protection laws. A Certificate of Destruction ( aka Data Erasure Certificate or Certificate of Sanitization) guarantees that data was destroyed with due diligence and the data cannot be recovered from the erased devices even after using advanced forensic data recovery techniques. CoD provides documented evidence that sensitive, critical, and confidential information was permanently destroyed, thereby eliminating the risk of data breaches, identity theft, and legal penalties.
Importance of Certificate of Destruction
A Certificate of Data Destruction acts as a pivotal document in lawsuits of data breaches to showcase that data was destroyed using a reliable tool or through services from an authorized vendor that provided the Certificate of destruction. Here are some of the benefits of this document that are meaningful to an organization:
-
Proof of Compliance
Every industry today is governed by legal requirements for how long data must be in use and maintained, but once the time limit of maintaining data is reached, the data must be securely destroyed. There are different methods of destroying data, as explained in the Data Destruction Knowledge Series. But, as an organization, whether you follow any method of destruction, maintaining a Certificate of Destruction is critical to staying compliant with global data protection laws like EU-GDPR, CCPA, SOX, GLBA, and HIPAA. CoD provides auditable proof of sanitization and promotes trust toward the third-party vendor performing media sanitization on behalf of your organization. Even the ISO 27001 standard obligates organizations to erase data securely when it has served its purpose and requires proof of erasure.
-
Data Destruction Verification Document
A Certificate of Data Destruction serves as verifiable proof that your data has been safely and securely destroyed using the appropriate technique or software. Auditors find CoD handy when verifying the data destruction process of a device or document. Software like BitRaser generates a Certificate of destruction after data is erased from drives and devices. The software also provides a Cloud console where the certificate of destruction can be stored at any time, anywhere access. The CoD comes in handy in both internal and external audits.
-
Peace of Mind
It is not only a document to meet compliance with data privacy laws and other industry regulations but also gives an organization and its stakeholders peace of mind that their data disposal strategy is sound and fail-safe. A certificate of destruction (CoD) ensures that no data breach incident or lapse has happened, as the document ensures complete, secure, and permanent data destruction.
- Safeguards Liability
The CoD acts as a liability protection document during episodes of legal disputes or data breaches. It helps businesses demonstrate that the devices were wiped off data and handled in accordance with the organization's data disposal guidelines.
-
NIST Mandates Data Destruction Certificate in its Guidelines
A Certificate of Destruction or Certificate of Data Sanitization, outlined in NIST SP 800-88 Rev 1, assists organizations or ITADs (IT Asset Disposition) companies in establishing a robust media sanitization program aligned with the NIST Guidelines for Media Sanitization. Appendix G (Page 56) of the NIST guidelines mandates organizations to keep a record of destruction and have it readily available on demand for any media destroyed.
Sample Certificate of Sanitization As Per NIST AppendixG
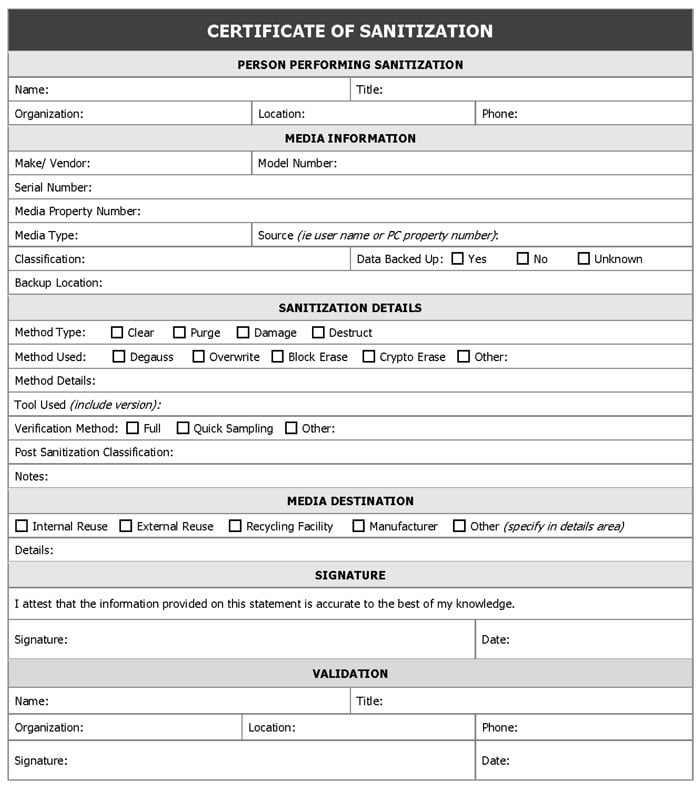
As per NIST, a few things should exist on a Certificate of Sanitization (or Certificate of Data Destruction) in some form to verify their authenticity and integrity. Let us look at the key components of the certificate.
Key Components of a Certificate of Destruction
The following elements are critical for an auditable certificate of destruction:
- A unique digital identifier to record the data destruction
- The model and serial numbers of the storage devices were erased or wiped
- Details of data sanitization method used
- Details of the verification method used
- Name of the Software used for Media Sanitization
- Name of Technician performing data destruction or sanitization
- Signature of the official verifying the disposal process
- Start Date and Time of the data sanitization process
Ensure that the tool or device used to erase sensitive data provides a 'Certificate of Sanitization' with accurate information. We recommend using BitRaser data erasure software that is tested and approved by NIST, Common Criteria, ADISA, and other bodies globally & provides all details as required for the Certificate of Destruction (CoD).
Note: Even new standards like IEEE 2883-2022 recommend documenting the sanitization results for compliance purposes, and a CoD is the best way to do this automatically using a software-based data destruction technique. You can see a comparison between NIST 800-88 and IEEE 2883-2022 to know more about these standards.
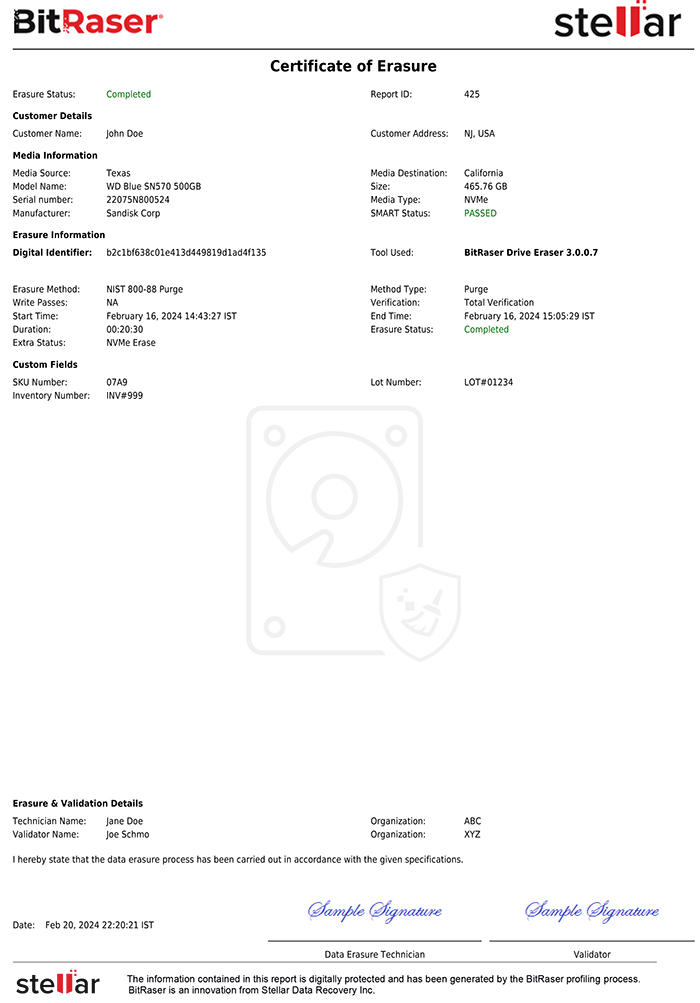
BitRaser Data Erasure Software Generates a Tamper-Proof Certificate of Destruction
- A Report ID and Digital Identifier along with software version and report date.
- Customer name and address.
- Data erasure summary including the total number of devices destroyed, method of erasure used (E.g., NIST 800-88 Purge or clear), number of passes (single or multiple), success and failure rate, work in progress (if any), verification method, etc. The certificate also mentions the start and end time of the process, along with the overall duration of the procedure.
- Hardware information includes manufacturer, chassis type, model name and UUID, system serial, USB hub, chassis serial, board serial, media source, and so on.
BitRaser Certificate of Data Destruction Template for Drive Eraser software.
View Complete Certificate
Download Sample BitRaser Certificate of Erasure
Being a documented proof of erasure, a Certificate of Destruction (CoD) ensures that an organization collecting, handling, or processing data acts responsibly by destroying data that is no longer required to ensure data privacy and protection as mandated by global regulatory norms. Hence, organizations must hire service providers or use software tools like BitRaser to generate a Certificate of Data Destruction as proof of data removal. It is a resilient approach to ensure that sensitive and confidential data stored on devices that are no longer needed is protected and is not exposed to bad actors, thereby mitigating liability risks. A CoD is more than just a document—it’s a safeguard against data-related liabilities and a cornerstone of responsible data lifecycle management.









