Data destruction is a crucial and evolving business need, considering the prodigious growth of data, storage devices, and data protection regulations. And, there are several ways to attain secure and compliant data destruction that you have read in Chapter 3 - Data Destruction Methods and Techniques of this knowledge series. However, a question lingers beyond understanding the technicalities of data destruction.
As an organization— how do you adopt these
data destruction techniques and practice them within your policy framework to
meet the various obligations?
Data
destruction policy is the answer that knits the backend
techniques, people, and processes into a unified system to enable rigorous and
consistent frontend execution. The efficiency and effectiveness of a
policy-driven data destruction practice, of course, depends upon the underlying
components and their inner workings defined in the policy document.
This chapter deep-dives into the subject of “data destruction policy”, focusing on its purpose, utility, and constituent components, namely— scope, procedures, security categorization, roles & responsibilities, and other nitty-gritty.
 Image: Hard Drive Destruction
Image: Hard Drive DestructionThese
details provide the building blocks to craft your own customized data
destruction policy that can drive robust and repeatable execution to meet the prevailing
compliance standards.
Introduction To Data Destruction Policy
A data destruction policy is the official documentation
of the principles and practices that guide an organization’s actions towards
attaining secure and compliant data disposal. The policy aims to design a
pertinent system and instruct people in the organization with precise actions
to meet the end goals of data destruction in order to maintain data privacy and
regulatory compliance.
A rigorously drafted policy can allow
organizations to navigate favorable data destruction outcomes across all the streams
& touchpoints in the data lifecycle.
For example, you might vividly imagine the ever-growing
customers’ data in your organization’s possession, acquired through
transactions like purchases, registrations, third-party acquisitions, etc. That
colossus data could be in multiple states at any given time, like data at rest,
in active use, and data in transit changing hands frequently.
A data destruction policy ensures that all this
information is destroyed forever beyond its intended use and consent terms.
Need & Benefit of
Data Destruction Policy
The following points enumerate the utility of a data
destruction policy, illustrating why every organization needs to have formal
policy documentation:
1. Helps Safeguard Against Data Breaches
A documented policy can ensure consistent and failsafe data destruction through all touchpoints and streams in an organization’s IT asset lifecycle, including the end-of-life and reallocation workflows. It can allow IT asset management teams to implement rigorously vetted data destruction practices across all units and subsidiaries of the organization and further maintain adherence.
2. Guides Data Destruction Basis the Type of Storage Media
A data destruction policy can provide precise guidance to destroy the data based on the media type. For example, physical destruction techniques for optical and tape media and likewise data erasure for hard drives & SSDs. Further, it can define specific protocols to destroy the different data types based on the sensitivity levels and security categorization (basis FIPS 199).
3. Defines the Ownership & Accountabilities
A well-articulated data destruction policy precisely defines the ownership and accountabilities in the storage devices’ chain of custody and demarcates the roles and responsibilities. It provides a precise “people-task” mapping with an escalation matrix to address potential gaps and contingencies in the data destruction process.
4. Ensures Compliance as per the Applicable Law(s)
Nearly every data protection law has provisions that mandate organizations to destroy consumer data, based on the explicit consent granted for data collection, storage, and processing. However, there could be subtle differences in the data destruction requirements laid down in these laws.
For
example, California Consumer Privacy Act (CCPA) empowers consumers with the
“right to delete”, allowing them to request deletion of their personal
information with a maximum notification duration of 45 days. Similarly, GDPR
has two broad provisions called “right to
erasure” or “right to be forgotten”
that mandate organizations to respond to the consumers’ request for their
personal data erasure within 30 days.
A
diligently drafted data destruction policy can play an imperative role in
helping organizations attain compliance with (all the) applicable data
protection laws— regional, local, and sectoral.
Data Destruction Policy: The
Building Blocks
This section explains the essential components of a
data destruction policy. Understanding these constituent elements can help you
define your organizational policy to drive
secure and compliant data destruction and scale the practice across scenarios
and facilities. The Building Blocks covered in this section are
- Purpose Statement
- Defining Scope of Data Destruction
- Security Categorization
- Media Control
- Legal Obligation
- Roles and Responsibilities
- Data Destruction Procedures
- Verification
- Record of Data Destruction
- Policy Enforcement
- Incident Reporting
 Image: Building Blocks
Image: Building Blocks
1. Purpose Statement
The purpose or goal statement serves as the guiding principle for the data destruction policy and plays a critical role in shaping the framework for scalable implementation. It provides a precise and objective statement of the outcomes expected by implementing the data destruction policy.
Sample purpose statement
This policy ver2.3 released 26 July, 2021 instructs all parties involved, including the program manager, data owner, information system owner, IT asset management team, vendors & other personnel, to adhere to the norms specified herein for safe and compliant data destruction. Key Goals of this data destruction policy ver2.3 implementation is to attain:
a) 100% data destruction across all data-bearding devices owned, operated, or contracted by <>.
b) Maintain tamper-proof audit trails for all target devices to serve monthly, quarterly, and annual audit requirements.
c) Maintain demonstrable readiness to meet planned and unplanned compliance audits for all the data protection laws applicable to the organization.
2. Defining the Scope of Electronic Data Destruction
The policy’s scope provides critical input to determine the optimal methods and techniques to attain the data destruction outcomes within the applicable constraints. The key scope areas include the following:
a) Storage devices
An organization might be dealing with a wide variety and quantity of data storage devices transitioning through different lifecycle stages. These devices could include hard disk drives, solid-state drives, USB flash storage, computers, servers, smartphones, optical media, magnetic tapes, card readers, printers, point-of-sale devices, IOT devices, etc. Further, the underlying data storage media could be magnetic, flash, hybrid, optical, paper, film, etc.
The policy should instruct the organization
to maintain a checklist inventory of all types and numbers of data storage
devices. It should also include the provision for maintaining the device
lifecycle stages and ownership details.
b) Data
A majority of consumer data is generically termed “sensitive” in privacy-related conversations. In reality, not all consumer data is considered sensitive. Further, the sensitivity levels could vary based on contexts like information type, user consent levels, use, and impact if the data is compromised. For example, personal data (anonymized personal information) is considered less sensitive than Personally Identifiable Information (PII), such as social security number, which can distinctly identify a natural person. Similarly, there are other types of sensitive data such as Protected Health Information (PHI), educational information, financial information, etc. The policy needs to account for all types of data in the organization’s possession.
c) Facilities & People
The data destruction policy needs to span all the facilities directly operated by the company or run by a third-party affiliate, including downstream e-recyclers. The data destruction mandates and practices for the different facilities should be based on factors like nature of operations, geographical location, operating conditions (for example, offline vs Internet-enabled), industry (retail vs banking vs manufacturing), etc. Further, all the people directly or indirectly associated with the organization need to have a clear mapping of their accountabilities and roles towards supporting the data destruction goals.
3. Security Categorization
The data destruction policy needs to define the security categorization in terms of the potential impact of events that danger the information. According to the Federal Information Processing Standard Publication 199 (FIPS 199) , “Security categories are to be used in conjunction with vulnerability and threat information in assessing the risk to an organization.”
FIPS 199 defines the following security categorizations based on the Information Types and Information Standards:
- Security categorization applied to information types: This categorization is determined based on the impact of compromised user information and system information. So, the policy should include a provision to segregate the data in tiers based on its security categorization to allow a focused and commensurate destruction approach.
- Security categorization for information systems: Security categorization of information systems requires a deeper analysis of the data storage systems and also needs to consider the security categorization of the information types residing in the information systems.
The generalized expression for this security categorization is:
SC information type = {(confidentiality, impact), (integrity, impact), (availability, impact)}
The acceptable values for potential impact are LOW, MODERATE, HIGH, or NOT APPLICABLE.
4. Media Control
Aside from defining the information security categorization, the data destruction policy also needs to specify the parties having control over the storage media at different points in time. Broadly, there are two control states viz. internal control and external control.
a) Internal
control: The
storage media is entirely under the organization’s internal control if it is
managed by the company’s in-house IT asset management team. Media handed over
to external vendors for maintenance or upgrade is also considered in the
organization’s control, provided the necessary agreements are in place to
secure data privacy and confidentiality. Further, “onsite” maintenance of
storage media by third-party vendors like MSPs and MSSPs under the
organization’s supervision also counts as internally controlled media.
b) External
control: The
storage media permanently leaves the organization’s ownership through
transactions like resell, return, and disposal for recycling. Here, the control
over the storage media and underlying data, if not destroyed, changes to the new
owner.
5. Legal Obligation
Over the past decade, data protection laws have grown in number and have become more focused and nuanced. There are hundreds of federal and state laws to protect data privacy in the US alone, including about 20 sectoral laws focused on finance, healthcare, etc. You can read this article for an overview of US data privacy laws.
The policy can
provide explicit guidance to meet compliance with the applicable laws. Here is
a compact grid indicating the “right to
delete” provision in some of the prominent data protection laws:
6. Roles and Responsibilities
The data destruction policy must precisely define the roles and responsibilities to ensure data protection through its entire lifecycle. As per NIST SP 800-88, the following are some pertinent roles and responsibilities within the organization:

a) Chief Information Officer (CIO) - This role
owns the information assets, including data security, integrity, and privacy
aspects, within the organization. The CIO (or sometimes the business unit head)
defines the policies and principles for data access and usage. They also
promulgate the data destruction principles as a component of the information
security policy and ensure that data destruction standards are met.
b)
Chief Information Security Officer
(CISO) – This role
is responsible for crafting the vision, strategy, and plan to protect the
organization’s information assets and ensure data security. The CISO role can
own and shoulder the overall “data protection” charter out of the broader CIO
role.
c)
Program Manager - This role is responsible for
establishing an effective data security governance structure and organizing the
resources for the program’s success.
d)
Data Steward - Data steward implements the
principles and policies laid down by the information owner (CIO or BU head).
The individual — aside from managing the data availability and quality — acts
as an interface between the business unit and IT asset management team to
ensure the destruction of sensitive information as necessary.
e)
Information System Owner - This role ensures the sanity of maintenance and contractual
agreements to adequately protect the storage system and data as per applicable
security categorization levels.
f)
Property Management Officer - This role is responsible for
ensuring redistribution of the storage media within the organization or to
external parties as applicable after data destruction.
g)
Records Management Officer - The records management officer
maintains detailed records of all types of information and advises the
information owner concerning the data retention requirements.
h)
Privacy Officer - The privacy officer provides
counselling on privacy issues concerning the data destruction process and
storage media. They also owns the responsibility of interpreting any deviations
in following the protocols and subsequent impacts, including data breaches.
i)
Users - They are responsible for knowing
the confidentiality of data they use and its safe handling to maintain the
privacy standards.
7. Data Destruction Procedures
The policy should lay down the data destruction procedure based on the optimal combination of techniques for the storage media types. NIST SP 800:88 Guidelines define a comprehensive media sanitization matrix using the Clear, Purge, and Destroy data destruction techniques.

Data
destruction location is another vital policy consideration,
decided on the basis of the chosen data disposal procedure(s). Broadly, there
are two options for data destruction location, namely onsite (on the company premises) and offsite (in a dedicated data destruction facility).
Onsite data destruction is performed using DIY data
erasure software or a degausser operated by a competent technician. Sometimes,
mobile shredding trucks operated by IT asset destruction (ITAD) service vendors
can also perform onsite data destruction provided the logistic and financial
constraints are met. In contrast, offsite data destruction can be performed
using data erasure software, degausser, or shredder.
Note:
Offsite data destruction poses inherent chain-of-custody risks to the data.
Therefore, the policy should consider including an explicit provision to
mandate “onsite erasure” of storage devices
before the organization releases the custody to the offsite service vendor.
NIST SP 800:88 Media
Sanitization Matrix
Storage Media |
Clear |
Purge |
Destroy |
Paper and microforms |
NA |
NA |
Shred using cross cut shredders |
Copier, printer, fax machine |
Device reset |
Use hardware or firmware specific techniques such as rewriting, block erasure, or cryptographic erasure |
Use standard physical destruction methods
- Shred
- Disintegrate
- Pulverize
- Incinerate
|
Routers and Switches |
Full factory reset as per OEM settings |
NA |
Use standard physical destruction methods |
Floppies |
Overwrite and verify |
Degauss
|
Incinerate |
Magnetic Disks |
Overwrite and verify |
Degauss |
Incinerate |
Storage Media |
Clear |
Purge |
Destroy |
Reel and Cassette Format Magnetic Tapes |
Rerecord (Overwrite) |
Degauss |
Incinerate |
ATA and SCSI Hard Disk Drives. Also applicable to local external HDDs. |
Overwrite and verify |
Use any of these methods:
- Overwrite EXT command
- Cryptographic Erase
- Use SECURE ERASE command
- Degauss
|
Use standard physical destruction methods |
ATA Solid State Drives |
Overwrite and verify
OR,
ATA SECURITY ERASE UNIT command, if supported |
- Block Erase
- Cryptographic Erase through the TCG Opal SSC or Enterprise SSC interface
|
Use standard physical destruction methods |
SCSI Solid State Drives |
Overwrite and verify |
- SCSI SANITIZE command
- Cryptographic Erase
|
Use standard physical destruction methods |
NVM Express SSDs |
Overwrite and verify |
- NVM Express Format command
- Cryptographic Erase
|
Use standard physical destruction methods
|
Storage Media |
Clear |
Purge |
Destroy |
Mobile devices
(iOS® and Android® devices) |
Erase all contents using Factory Reset
OR,
Overwrite and verify |
eMMC Secure Erase or
Secure Trim command for factory reset
OR,
Cryptographic erase |
Use standard physical destruction methods |
USB Removable Media and Memory Cards |
Overwrite and verify |
Not supported |
Use standard physical destruction methods |
Embedded Flash Memory |
Reset to original factory settings |
Not supported |
Use standard physical destruction methods |
DRAM |
Not supported |
Remove the DRAM from the device after switching off the power. |
- Shred
- Disintegrate
- Pulverize
|
EAPROM |
Not supported |
Full chip purge as per OEM datasheet |
- Shred
- Disintegrate
- Pulverize
|
EEPROM |
Overwrite and verify |
Not supported |
Use standard physical destruction methods |
Optical Media |
Not supported |
Not supported |
- Shred
- Disintegrate
- Incinerate
|
[2] Standard physical destruction methods include Shredding, Disintegration, Pulverization, Incineration
[3] DRAM - Dynamic Random Access Memory
[4] EAPROM - Electronically
Alterable PROM
[5] EEPROM - Electronically
Erasable PROM
8. Verification
Data destruction alone is not sufficient. The policy should include a provision to systematically verify the results of a given data destruction procedure vis-à-vis the target storage media. The policy can ideally address this need through a two-step process that mandates verification after every data destruction process and random sampling of the devices.
Aside
from data destruction process, the verification scope also includes
checking the equipment and personnel efficacy. According to NIST SP
800-88 Guideline, “If the organization is using sanitization tools (e.g., a
degausser or a dedicated workstation), then equipment calibration, as well as
equipment testing, and scheduled maintenance, is also needed.”
Further,
the policy needs to include provisions for conducting regular assessments and
training of data destruction personnel. This step is critical to ensure
sufficient competence to run the data destruction tools and equipment.
9. Record of Data Destruction
Traceable and immutable records of data destruction are crucial to meet compliance by supplying the necessary audit trails. Therefore, the policy should include provisions for systematic recordkeeping of all the data destruction processes conducted in-house or by third-party vendors. Tamperproof certificates and reports of data destruction, maintained for individual storage media, can help businesses maintain the necessary documentation for compliance. NIST SP 800-88 recommends capturing the following details in the data destruction records:
- Manufacturer
- Model
- Serial Number
- Organizationally Assigned Media or Property Number (if applicable)
- Media Type (i.e., magnetic, flash memory, hybrid, etc.)
- Media Source (i.e., user or computer the media came from)
- Pre-Sanitization Confidentiality Categorization (optional)
- Sanitization Description (i.e., Clear, Purge, Destroy)
- Method Used (i.e., degauss, overwrite, block erase, crypto erase, etc.)
- Tool Used (including version)
- Verification Method (i.e., full, quick sampling, etc.)
- Post-Sanitization Confidentiality Categorization (optional)
- Post-Sanitization Destination (if known)
- For Both Sanitization and Verification:
- Name of Person
- Position/Title of Person
- Date
- Location
- Phone or Other Contact Information
- Signature
- Data backup details (optional)
Ready availability of data destruction records is another crucial aspect the policy needs to consider. Aside from providing a tamper-proof audit trail, the data destruction record — if available instantly & anytime on-demand — can spare the organization the hassle of producing proof of data destruction within the due time.
Imagine
a customer demanding the proof of executing her “right to erasure” request;
delay in producing the necessary records can lead to hefty penalties for the
company as per the applicable data protection laws.
View sample reports and certificates for the data erasure method:
https://www.bitraser.com/reports-and-certificates.php
[View sample report]
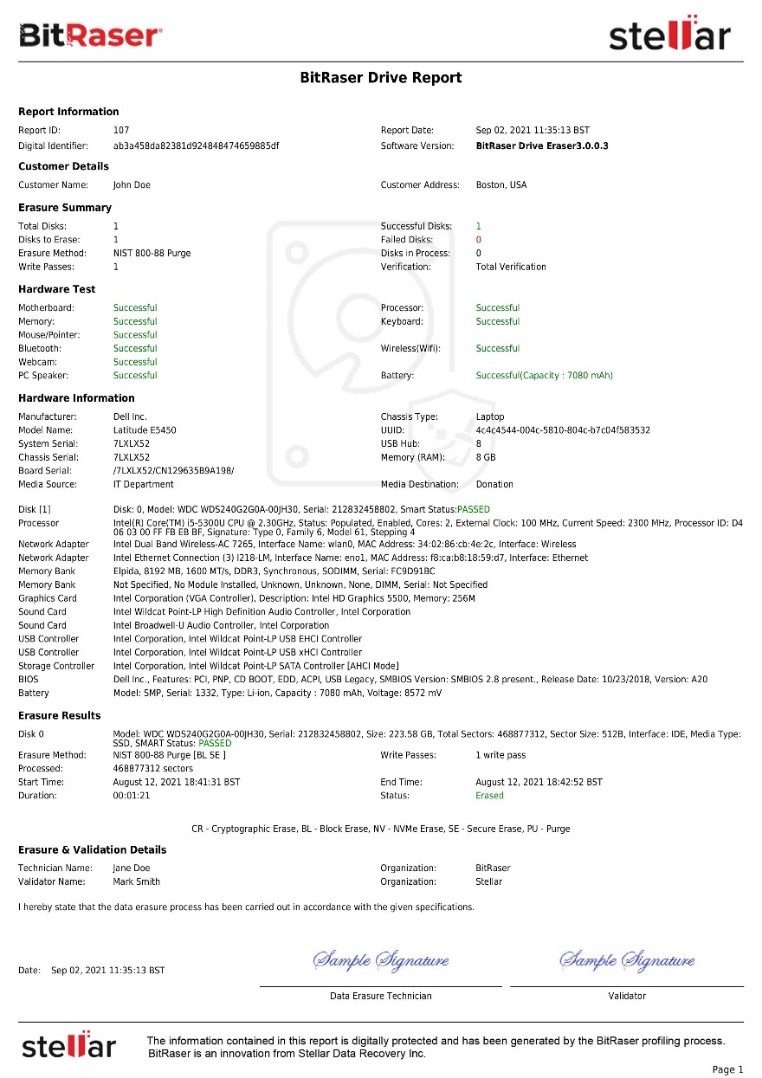
View Complete Report
Image: Sample Erasure Report Generated by a Data Erasure Software 10. Policy Enforcement
The policy needs to define formal mechanisms such as internal and/or third-party audits that ensure adherence to the protocols. It’s the organization’s prerogative to determine the provisions for policy violations and data breach notifications; however, the organization should align these provisions with the prevailing legislation. The violation levels should be specified in tiers based on the number and extent of violations and their overall impact. Further, the policy needs to determine the commensurate penalties.
Appeals and committee review
processes are other critical aspects of data destruction policy enforcement.
Accordingly, the policy should include a provision to allow appealing
contentious violation. Subsequently, a board or committee comprising the
company’s privacy officer, government representative, and other parties can
preside over it.
11. Incident Reporting
The data destruction policy needs to include a provision for reporting actual and suspected data breach incidents. Such a provision can facilitate prompt reporting of lapses and allow mitigation through clear mapping of the points of contact and hierarchical matrix within the organization.
Data Destruction Policy: Best
Practices
The following are some of the best practices when
drafting your organization’s data destruction policy:
1) Purpose statement:
Draft a simple and overarching goal statement with quantifiable success metrics to the extent possible.
2) Application scope:
Try to maximize the policy’s application scope for comprehensive coverage against unforeseen and emergent circumstances. You can define a tiered implementation to get optimal results vis-à-vis the input efforts and resources.
3) Media control:
The policy can emphasize adopting automated mechanisms like a tool or software can help you get a firm grip on the media control component. Integrating the data destruction workflow with business systems like ERP can be immensely helpful especially, if your organization handles a vast number and variety of data-bearing devices.
4) Roles & responsibilities:
The policy documentation can define a visual map illustrating various elements like the workflow, hierarchy, and interrelationships of all the roles involved in the data destruction process. This map could enable a general, organization wise visibility to map accountabilities and trigger escalations where required.
5) Verification:
The random testing provision in the policy should ideally be conducted by people that were not part of the data destruction personnel deployed for the media lot. Further, a different verification method or tool could be used to have a more robust verification process.
6) Documentation:
The data destruction policy can emphasize the need to maintain “up-to-date” repository of data destruction reports and certificates for individual devices. It could mandate the use of professional tools or software to automate documentation and maintain 24x7 access. Further, inclusion of provisions like cloud repository data destruction records can allow failsafe compliance.
7) Test implementation:
Before releasing the data destruction policy, the organization can consider a test implementation to determine any loopholes or make new discoveries in the system. Also, tiered implementation in phases and at different levels can allow iterations while scaling the practice.
8) Policy review and updates:
Include a process to review the policy document at a defined frequency for addressing new developments like data privacy laws, clauses, business expansion into a geography or market segment, etc. This step could ensure that a well-drafted policy stays current and relevant in the evolving data privacy landscape.
Conclusion
A formal policy provides the imperative framework to
shape the data destruction practice and scale it to meet the organization’s
needs. Nonetheless, drafting a policy is an arduous task demanding a broad
consideration of aspects like scope, type of information, legislation, etc.,
with direct or implied implications on the compliance outcomes.
We hope this chapter demystified the subject of data
destruction policy and helped you gain a better understanding to allow drafting
customized policy documentation for your organization. After understanding the significance of data destruction, its growing eminence, and the appropriate data destruction methods that are guided by a policy framework, you need to know the global standard and guidelines that direct your data destruction policy towards global guidelines and standards for data erasure.
Read Chapter 5 of Our Knowledge Series on Data Destruction Standards & Guidelines














