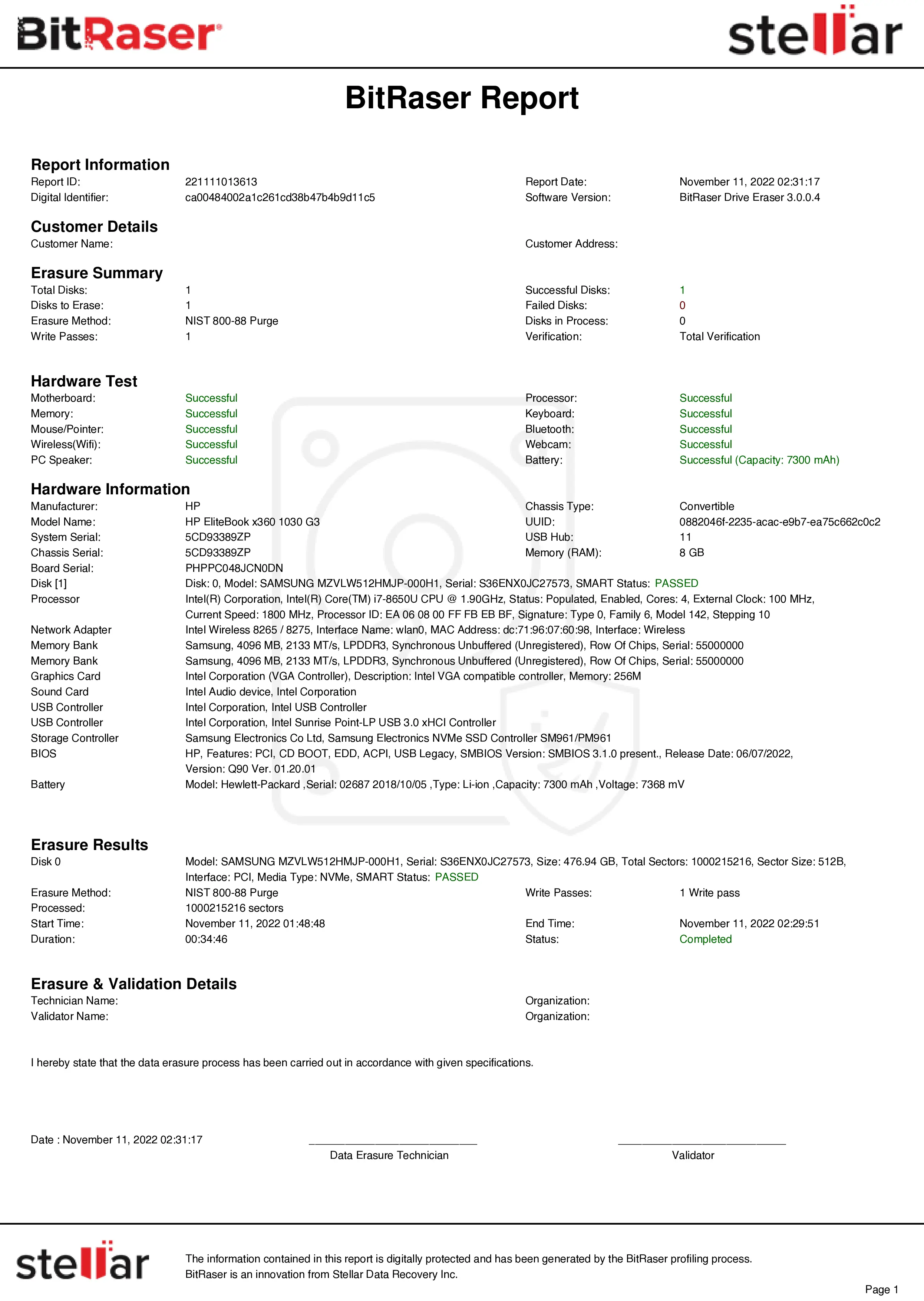
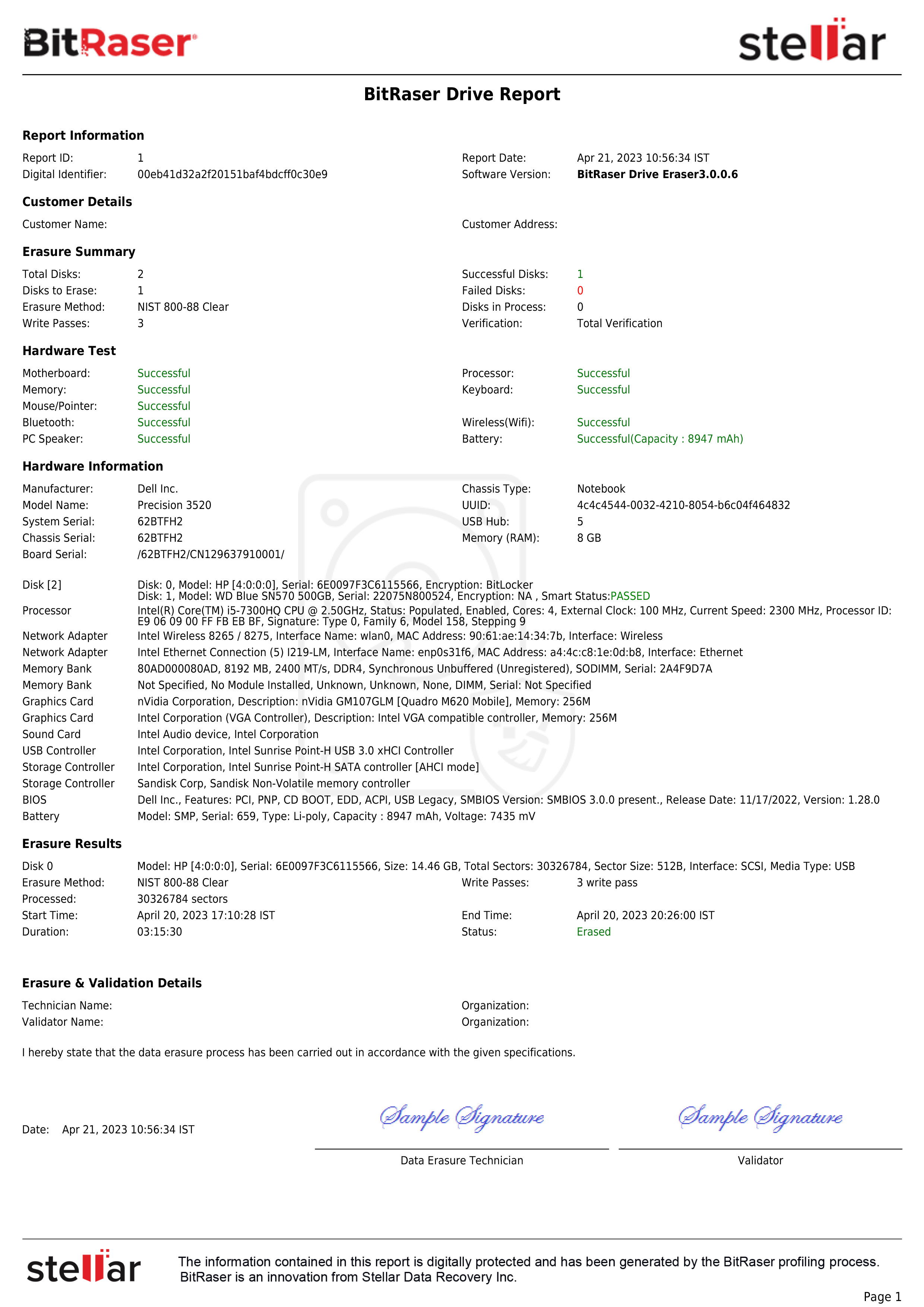
In this KB we will explain NIST Clear & Purge methods, and provide instructions for securely erasing drives using NIST 800-88 standard.
Modern hard drives inside computers and servers can store humongous data reaching terabytes in size. Protecting this data from leakage and breaches is crucial for organizations, significantly when the hard drive’s custody or ownership changes. For example, an organization may need to dispose of the used hard disk drives, solid-state drives, or devices with built-in storage, or it might be returning the storage devices acquired on lease.
In such scenarios, the organization needs to erase the hard drives following the standard procedures to ensure the permanent removal of the complete data in line with applicable data protection laws. Data erasure and other media sanitization procedures are essential protocols in the IT asset management policies of such privacy-focused organizations.
Several standards govern the media sanitization procedures, including data erasure. NIST 800-88 is one such prevalent standard, providing in-depth coverage on media sanitization types, implementation techniques, usage scenarios, etc.
NIST 800-88 suggests Clear and Purge as the two methods to overwrite (i.e., erase) the target data on a hard drive using a mix of logical and physical techniques.
NIST Clear Method for Hard Drive Erasure
NIST Clear method is based on erasing the data stored in all user-addressable locations on PATA, SATA, eSATA, and other ATA hard disk drives (HDD). The goal of the Clear method is to overwrite the storage sector with non-sensitive values using non-invasive read/write commands.
The Clear method can also involve factory resetting the device if rewriting is not supported. NIST 800-88 Clear method recommends using at least a single write pass with a fixed value to overwrite the drive. It also suggests using the SECURITY ERASE UNIT command to overwrite the SSD, if supported.
NIST Purge Method for Erasing HDD & SSD
NIST 800-88 Purge method uses physical or logical techniques to render the HDD or SSD data unreadable and irretrievable using data recovery tools or methods. There are multiple ways to implement NIST Purge for overwriting the data :
- Cryptographic Erase (CE) is used for the erasure of a Self-Encrypting Drive (SED). SEDs are hard drives with integrated and always-on encryption of data, enabled using a cryptographic key directly accessible to the device. The Cryptographic Erase technique sanitizes the target data’s encryption key such that the encrypted data cannot be decrypted and thus turns into an unrecoverable state.
Cryptographic erasure is an efficient and straightforward method to sanitize SEDs; however, its efficacy depends on the cryptographic key or algorithm’s strength. NIST 800-88 guideline states that Federal agencies must use FIP 140 validated encryption modules to attain the required level of assurance with CE. NIST guidelines also suggest that Cryptographic Erase should not be used if a hard drive has unencrypted data or if the data's encryption status is unknown.
- Overwrite EXT Command involves overwriting the data on a hard drive using a single pass of a fixed pattern such as zeros or a pseudorandom pattern.
- Block Erase Command is used to erase flash memory devices such as solid-state drives by setting the voltage level on the individual storage elements to a substantially higher value than the normal voltage and dropping it to zero. NIST 800-88 guideline suggests writing the block erased SSD with binary 1s on all the user addressable memory locations followed by a second block erase command on the media. Alternatively, it recommends using the Secure Erase command if Block Erase is not supported on the SSD.
Data Erasure Software for Secure Erasure of Hard Drives
There are specialized data erasure software tools aside from the manual commands to sanitize a hard disk drive and SSD, such as those based on the NIST 800-88 Clear and Purge methods. These software tools can securely erase a hard drive, computer, server, network printer, and even mobile device. Compared to manual techniques, data erasure tools can offer a more efficient, hassle-free, and comprehensive solution for wiping hard drives. Professional data erasure software can even facilitate systematic documentation to facilitate regulatory compliance.
However, before adopting data erasure software and making it a part of your media sanitization strategy, do consider a few important aspects. Firstly, the software should be able to wipe the hard drive as per the prevalent standards like NIST 800-88, DoD, etc. ensuring the data is indeed erased as per a globally recognized standard and is removed forever. The tool should be able to automate the erasure process and reduce human intervention. And, it should have a systematic way to generate the documents to sufficiently support the audit and compliance needs.
For example, BitRaser Drive Eraser is a certified data erasure software for the erasure of hard drives in line with global standards. It generates tamper-proof reports and certificates of erasure for failsafe compliance with regulatory norms. The following is an outline of the instructions for using BitRaser:
Steps to wipe a hard drive using BitRaser Drive Eraser:
Note: BitRaser Drive Eraser can start wiping a hard drive in less than 10 minutes. The following is a broad outline of the instructions for using BitRaser to wipe one or multiple hard drives. Visit the BitRaser deployment guide for detailed stepwise instructions
Requirements:
- Blank USB: 2 GB or more for creating a bootable wiping media
- Internet: Ethernet or Wi-Fi
- Storage rack for mounting the hard drives
Stage 1: In this stage, you need to log in to your BitRaser cloud account and download the BitRaser Drive Eraser ISO file.
Stage 2: In this stage, you create bootable media by burning the BitRaser Drive ISO on a USB drive. The bootable USB allows you to wipe an entire hard drive without installing the software.
Stage 3: In this stage, you erase the hard drive(s) using the bootable USB. You need to mount the hard drive in the storage rack connected to a host machine. Next, you insert the bootable USB drive, choose the hard drive(s) from the boot menu, and start wiping them.
After erasing the hard drives, BitRaser Drive Eraser generates digitally signed reports for all the drives and saves them automatically to your BitRaser Cloud account. You can access the reports using your credentials.
Refer to the BitRaser deployment guide for detailed instructions on how to wipe a hard drive.
FAQs
How do you secure erase a hard drive? 
You can use overwriting software like BitRaser to securely erase your hard drive.
What is the NIST 800-88 standard? 
NIST 800-88 is a prevalent standard providing in-depth coverage on media sanitization types, implementation techniques, usage scenarios, etc.
What is the NIST Purge? 
NIST 800-88 Purge method uses physical or logical techniques to render the HDD or SSD data unreadable and irretrievable using data recovery tools or methods.
What is the difference between Purge and Clear? 
NIST Clear method overwrites the storage sector with non-sensitive values using non-invasive read/write commands. In contrast, NIST Purge uses physical and logical techniques making data recovery impossible.
Does a factory reset wipe the hard drive? 
Despite factory resetting, data can still be recovered using data recovery software. However, you would require data erasure software for wiping data beyond recovery.