Data erasure and sanitization methods can vary in effectiveness and the level of security they provide. Therefore, it is important to choose a method appropriate for the data's sensitivity and the level of protection required. In most developed nations, the government sets up its own standards.
There is NIST 800-88 in the USA, British HMG InfoSec Standard 5, Australian Government ICT Security Manual 2014, Standard VSITR of Germany Federal Office for Information Security, and so on. Likewise, the Canadian government follows ITSP.40.006 v2. It follows the CSEC ITSG-06 data erasure process.
RCMP TSSIT OPS-II preceded the ITSP.40.006 v2 data sanitization protocol. A summary of RCMP TSSIT OPS-II and ITSP.40.006 v2 is discussed below.
A Brief Look at RCMP TSSIT OPS-II
RCMP TSSIT OPS-II used to be a software-based data erasure mechanism used by the Canadian government in the past. It used multiple passes of overwriting:
- Pass 1. Write a zero.
- Pass 2. Write a one.
- Pass 3. Repeat Pass 1.
- Pass 4. Repeat Pass 2.
- Pass 5. Repeat Pass 1.
- Pass 6. Repeat Pass 2.
- Pass 7. Write any character
In the end, verify that every sector has been written over. This is very similar to the DoD 5220.22 M 7 pass method.
Benefits of RCMP TSSIT OPS-II
The RCMP TSSIT OPS-II was one of the most dependable data erasure methods.
Why use RCMP TSSIT OPS-II
- Six individual passes of 0, and 1 with one random character 7th pass was sure to wipe out any data.
- It is among the best if you wish to use a rigorous pattern.
- Performs one verification at the end, unlike the DoD 5220.22 standard, which saves time.
- Using a random character at the end adds to the security.
Drawbacks of RCMP TSSIT OPS-II
- 7 passes take very long to write, especially for modern drives that are several terabytes in size.
- Overwriting multiple times on SSDs reduces lifespan. So it is not desirable.
The Canadian government no longer uses this old standard but has shifted to ITSP.40.006 v2.
Canada's New IT Media Sanitization Standard ITSP.40.006 v2
Background
The ITSP.40.006 v2 came into effect in 2017. It was issued by the Chief Communications Security Establishment (CSEC). ITSP.40.006 v2 is a comprehensive document that offers guidance for Canadian government departments and other IT practitioners.
Note that such publications are not law. For example, a Canadian can throw away his firm's hard disk without sanitizing it, but the guidelines are useful.
The Government of Canada (GC) has to use hundreds of thousands of pieces of IT equipment, from optical discs to tablets and laptops. This guide instructs departments on how to handle end-of-life disposal. Residual data might remain and prove to be dangerous in the hands of nefarious elements.
Source: https://cyber.gc.ca
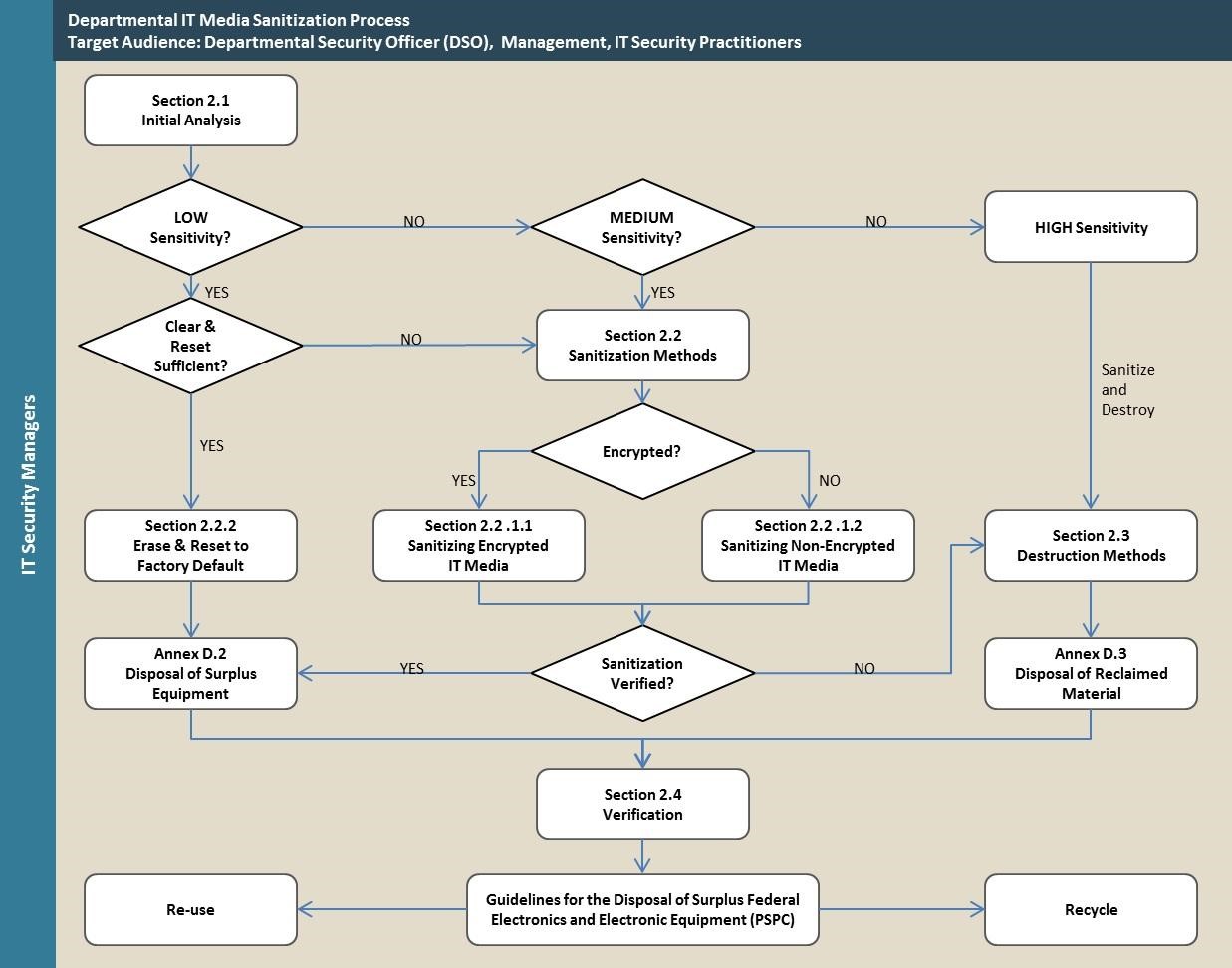
How is ITSP.40.006 v2 Implemented?
The ITSP.40.006 v2 document is long and detailed. The CSEC ITSG-06 is the actual data-wiping protocol. It is a part of the broader ITSP.40.006 v2
We offer a synopsis of the contents.
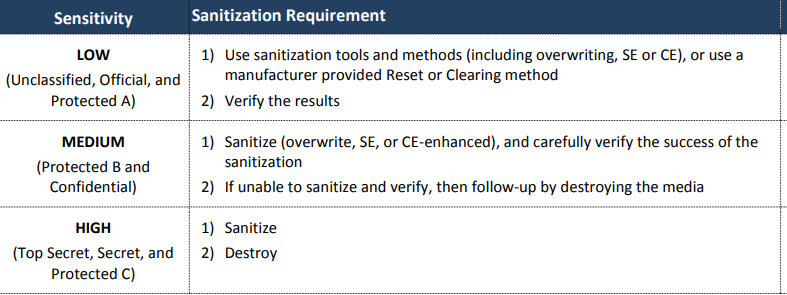
Sensitivity
- Media is classified according to low, medium, and high sensitivity. For example, The backup of old payroll records of a local city municipality is low sensitivity. Who wants to know what John P was paid in overtime during the winter of 2006? The usual business of the government is medium sensitive, especially if it relates to tax collection, budget projections, etc. Government has to publish the facts and figures in any case. Material related to foreign policy, terrorism, defense, defense factories, diplomatic chatter, and so on is highly sensitive.
Level of Threat
Sensitivity needs to take into account the level of threat.
- Low-sensitivity media will be secure against low-grade and unsophisticated hackers. These are adversaries on the lookout for low-hanging fruit and may not make a huge effort to reverse-engineer the data.
- Medium-sensitivity media has to be secure against well-trained hackers who command moderate resources.
- High-sensitivity media has to be secure against extremely sophisticated hackers with abundant resources.
A foreign government has no interest in Canadian municipal records or how the Department of Agriculture subsidized cattle inoculation. Instead, they want to know what is in the defense pipeline and what weighty matters the Cabinet is debating.
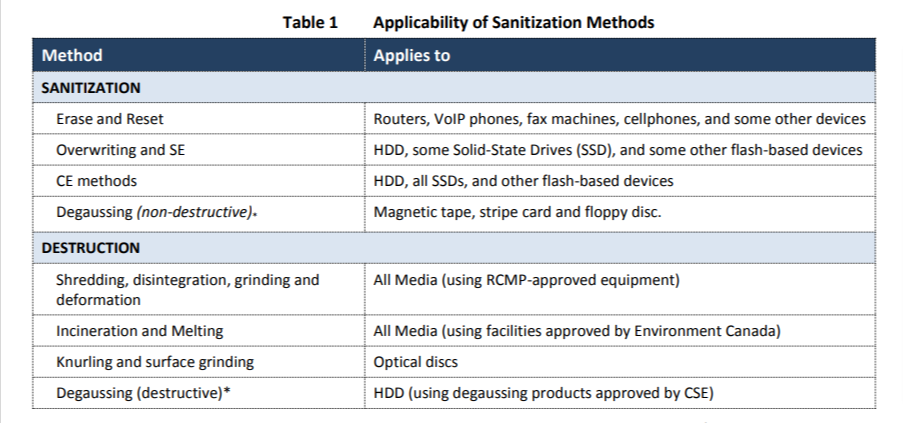
Sanitization Methods Prescribed by ITSP.40.006 v2.
The principal sanitization methods are:
1. Erase-and-Reset:
A reset is a process that restores a device, such as a smartphone and a router, to its original manufacturer settings. This process is often used to remove personal data before selling or giving the device away. To perform a factory reset of a device, you will need to go into the device's settings menu and look for an option to reset the device to its factory default settings. This option is usually found in the settings menu. When you perform a factory reset, all the data on the device, cryptographic certificates, and personal information will be deleted, and the device will be restored to its original state as it was when purchased.
2. Overwriting Data:
Overwriting is the process of writing new data over existing data on a computer or other digital device. Overwriting is often done to delete or erase the old data permanently. Several methods can be used to overwrite data using the software. Patterns of 1s and 0s are the most commonly used by data erasure algorithms.
Note: Deletion leaves behind the data; hence, secure erase is used to overwrite data with zeros or other patterns. This method is more effective at permanently erasing data than simple deletion.
Type of Overwrite
Section 2.2.3 of ITSP.40.006 v2 mentions the overwrite details as per the CSEC ITSG-06.
Pass 1. Write a 0 or 1.
Pass 2. Write the complement of 0 or 1 in Pass 1.
Pass 3. Write a random character.
- A single pass is deemed enough for new hard disks.
- Three passes are required for old hard disks that are less than 15 GB.
- Pass 1 and 2 are deemed enough for Solid State Drives.
- Every erase has to be verified.
3. Crypto Erase
Crypto Erase is a feature of some self-encrypting storage devices, such as solid-state drives (SSDs) and hard disk drives, which allows the user to permanently delete all of the data on the device and render it unrecoverable. When Crypto Erase is used, the device's encryption keys are deleted, rendering the encrypted data on the device completely unreadable. This process is usually performed by entering a command in the device's firmware or through a software utility provided by the manufacturer.
Crypto Erase is not a secure method of wiping data, especially if a backup of the encrypted keys is taken and not all backups are destroyed. If the key is discovered, there is a chance of recovery.
4. Degaussing
Degaussing is a process used to destroy data on magnetic storage media, such as hard disk drives. It involves exposing the media to a strong magnetic field, which removes the magnetic charges used to store data on the media. Degaussing is often used as a method of permanently deleting data when disposing of old computer equipment or storage media like hard drives and tapes. It is a secure physical method of data destruction and renders the storage media unusable, thereby destroying the media. However, degaussing is not advisable as it does not work on modern storage media like NAND Chip-based SSDs.
Source
Next, we've summarized the recommended destruction methods (where information is highly sensitive and classified as Top Secret, Secret, or Protected C)
The next table describes the recommended destruction methods for different types of media.
| Media Type |
Destruction Method |
| Optical media: CD, DVD, and Blu-Ray optical disks |
Reduce discs to small pieces < 10mm2
(1/8 x 1/8") or less if the destruction equipment is
capable; or
Grind the disc surface to remove the colored data layer, leaving only a semi-transparent
plastic disc (CDs only).
|
| Magnetic Media: HDDs, floppy discs, magnetic stripe cards, and magnetic tape |
Sanitize and then destroy by reducing to pieces (discs <40mm2 or tape <6mm); or
If unable to sanitize and verify, then reduce to pieces <10mm2
(1/8 x 1/8") or smaller.
|
| Solid-State and Flash Drives |
Sanitize, then destroy to pieces < 40mm2
in area (e.g. ¼ x¼"); or, if unable to sanitize, destroy
the device or storage components to particle size < 2mm.
|
| Smartphones and Tablets |
Sanitize, then destroy to pieces <10mm2
(1/8 x 1/8"); or if unable to sanitize, then destroy to
particle size < 2mm.
|
| Network Devices: Multi-function devices |
MFDs: Clear internal storage, then remove and destroy storage components |
Verification
Sanitization of the Media must be validated to safeguard the confidentiality of organizational data on the Media. There are two kinds of validation:
- Checking each and every memory location
- Check a representative sample of memory locations
The efficiency of sanitization varies depending on the technology a media device uses. Traditional sanitization processes may be ineffective, making verification difficult or impossible. If media verification cannot be completed using an alternative sanitization method that can be used that can be verified.
Data Erasure is Vital: Use ITSP.40.006 v2 Compliant Erasure Software.
Data erasure and sanitization is the process of securely deleting or destroying data stored on a computer or storage device. Data erasure is vital for every organization dealing with customer, investor, and employee data. The goal is to make the recovery of the original data impossible. This is achieved either by overwriting it with patterns following erasure standards or physically destroying the storage media.
BitRaser is a software tool designed to permanently delete data from hard disk drives (HDDs), solid-state drives (SSDs), and external drives. The state-of-the-art software runs off a bootable USB and can erase multiple devices simultaneously. Most importantly, it generates an audit trail with details of the erasure performed and the method used on the device to wipe all data stored on it securely.
BitRaser can delete data using every major data erasure guideline, including Canadian CSEC ITSG-06.
When you deploy BitRaser for secure data erasure, you never have to worry about data breaches or information falling into the wrong hands. Instead, donate and reuse your old IT equipment and reduce e-waste the smart way.









